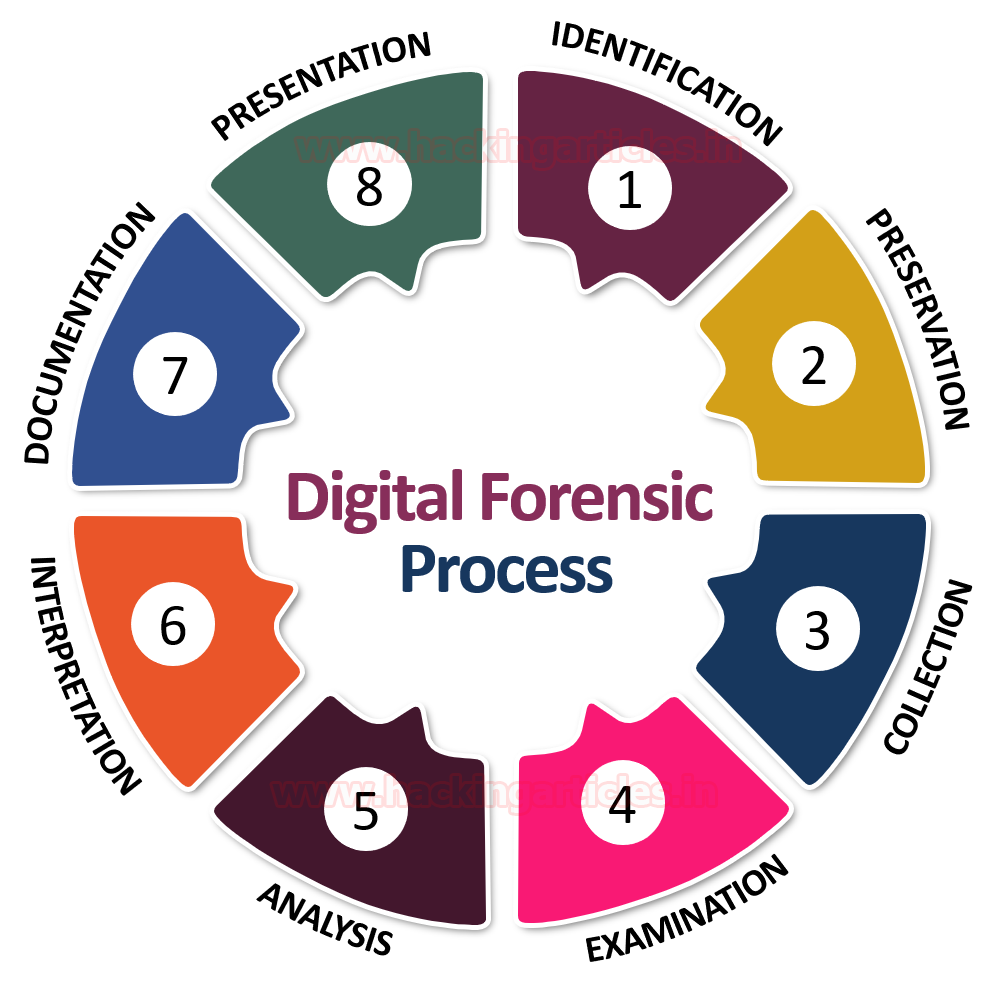
Digital Evidence in criminal investigations provides the reader with a better understanding of how digital evidence complements “traditional” scientific evidence and examines how it can be used more effectively and efficiently in a range of investigations.
Digital forensics is the process of uncovering and interpreting electronic data. The goal of the process is to preserve any evidence in its most original form while performing a structured investigation by collecting, identifying and validating the digital information for the purpose of reconstructing past events.
Cyber Law Consulting provides following services:
Collection of evidence from the incident site with accurate precession.
Disk & Hardware imaging of the suspected computer, mobile or other related hardware etc in scientific way so that all details are recorded upon.
Systematic verification and recording of the evidence collected.
Decrypt and access protected files.
Recovering as much deleted information as possible using application that can detect and retrieve deleted data.
Analyze special areas of the computer’s disks, including parts that are normally inaccessible.
All types of data imaging and analysis techniques as per the situation and requirements.
Critical analysis of each and every component collected as evidence using modern investigation techniques by our techno-legal experts.
Making concise, technically precise conclusions and preparing reports.
Our reports are legally acceptable and have been considered as evidences in various trials.
Our investigations have turnaround time (TAT) which is amongst the best in the digital forensics investigation field.
Information Security Audit & GAP analysis:
An Information security audit is a systematic evaluation of the cyber security of a company’s information system by measuring how well it conforms to a set of established criteria. The companies are expected to follow reasonable security practices to protect them under Section 43-A of IT Act, 2000.
Cyber Law Consulting provides following services:
We do a systematic study and evaluation of existing cyber security/IT policy of the corporate.
We do a Gap/Variance analysis of the existing cyber security/IT policy with reasonable security practices as per section 43-A of the IT Act, 2000
We provide a detailed report along with in depth analysis of what are thev gaps and how the same can be bridged upon.
Our findings, analysis and suggestions are concise, technically precise, practically feasible and legally.
Our turnaround time (TAT) is amongst one of the best in industry.Cloud Forensics:
Cloud network forensics is necessary because of attackers trying to hack the cloud services. We need to be notified when hackers are trying to gain access to our cloud infrastructure, platform, or service.
Cyber Law Consulting provides following services:
Data collection which includes identifying, labeling, securing, recording, acquiring, forensic data of client as well as network provider located on the network infrastructure.
Resource pooling of the potential data points.
Segregation and data analysis of the collected data.
Evidence examination and evidence analysis.
Virtualization to create a stimulated environment to understand the situation of crime.
Developing proactive measures to avoid repetion of any crime instances in future.
To prepare an in depth analytical report with findings and recommendations
Robot Forensics:
The coming years are certain to be critical for the robotics industry, as it refines the capacity to massively produce robots. As this shift takes place, these robots will increasingly become integrated into our everyday lives.
Cyber Law Consulting provides following services:
Imaging of Memory of the robotic device in question.
Cloning of Memory of the robotic device in question.
Physical hardware analysis of the robotic device in question.
Metadata analysis of the robotic devices.
IP address tracking of controller of robotic devices.
Confidential Reports of the analysis along with findings and suggestions.
Drone Forensics:
A branch of digital forensics encircling the recovery and investigation of drone device found in crimes is referred as “Drone forensics”. Basically drone is wireless device so its forensic is subsystem included in wireless forensic model as a server is also involved in the operation, drone is being controlled by the Server in the ground level. So Drone forensics involves the forensics of the server present at ground level where information is being transferred and stored and the forensic of the drone device. Here the prime focus is to discuss the Forensic Ontology for drone camera.
Cyber Law Consulting provides following services:
Imaging of Memory of the robotic device in question.
Cloning of Memory of the robotic device in question.
Physical hardware analysis of the robotic device in question.
Metadata analysis of the robotic devices.
IP address tracking of controller of robotic devices.
Confidential Reports of the analysis along with findings and suggestions.
Mac Analysis:
Collecting and analyzing RAM on a Mac is, not surprisingly, different than it is on a Windows machine. Tools like MacQuisition can assist examiners in acquiring RAM from Mac computers. Some Differences on a Windows machine running a live memory capture is normally fairly easy; as long as the user has logged in as an administrator, a memory capture tool can be run. In order to access RAM on a Mac, examiners need to enter the administrator’s password, regardless of who is logged in to the computer.
Cyber Law Consulting provides following services:
Imaging of Memory of the robotic device in question.
Cloning of Memory of the robotic device in question.
Mobile & GPS imaging and analysis of all versions apple iphones and tabs.
Imaging and analysis of all external drives, USB, SD cards, I pods which are exclusively apple compatible.
Email Analysis from the email servers which are exclusively configured to apple devices.
Confidential reports of the analysis along with findings and suggestions.
CCTV Analysis:
CCTV images are captured to a mixture of analogue tape based recording systems through to the latest digital video recorders (DVR). Forensic video analysis has been described as the scientific examination, comparison and/or evaluation of video in legal matters.
Cyber Law Consulting provides following services:
Image Analysis of the live capture feeds from DVR.
Imaging and cloning of the data stored from CCTV.
High resolution image analysis.
Data Analysis of the imaged and stored data.
Confidential reports of the detailed analysis along with findings and suggestions.
